5 Common Cybersecurity Threats Businesses Face Today (And How to Mitigate Them)

According to a recent report by Check Point Research, organizations globally experienced a 28% increase in cyberattacks in the first quarter of 2024 compared to the previous quarter. This translates to an average of 1,308 attacks per organization per week, highlighting the relentless nature of cyber threats.
This underscores the fact that cybersecurity can no longer be an afterthought for businesses today, which rely heavily on online operations and data storage. Regardless of size or industry, every organization is a potential target for cybercriminals. These criminals employ a diverse range of tactics, from phishing emails to sophisticated malware attacks, to gain unauthorized access to sensitive information, disrupt operations, or extort money.
With the purpose of raising awareness and providing plausible solutions, this article will cover five of the most common cybersecurity threats businesses face today. We'll walk through how these threats work and the potential damage they can inflict. Most importantly, we'll provide actionable strategies to mitigate these risks and protect your valuable data and systems. By implementing the right measures, businesses can notably improve their cybersecurity posture and operate with greater confidence.
Phishing & Social Engineering Attacks
Even with the best security software, a significant security risk lies in human vulnerabilities. Phishing and social engineering attacks take advantage of these vulnerabilities by manipulating people into giving away sensitive information or malicious links.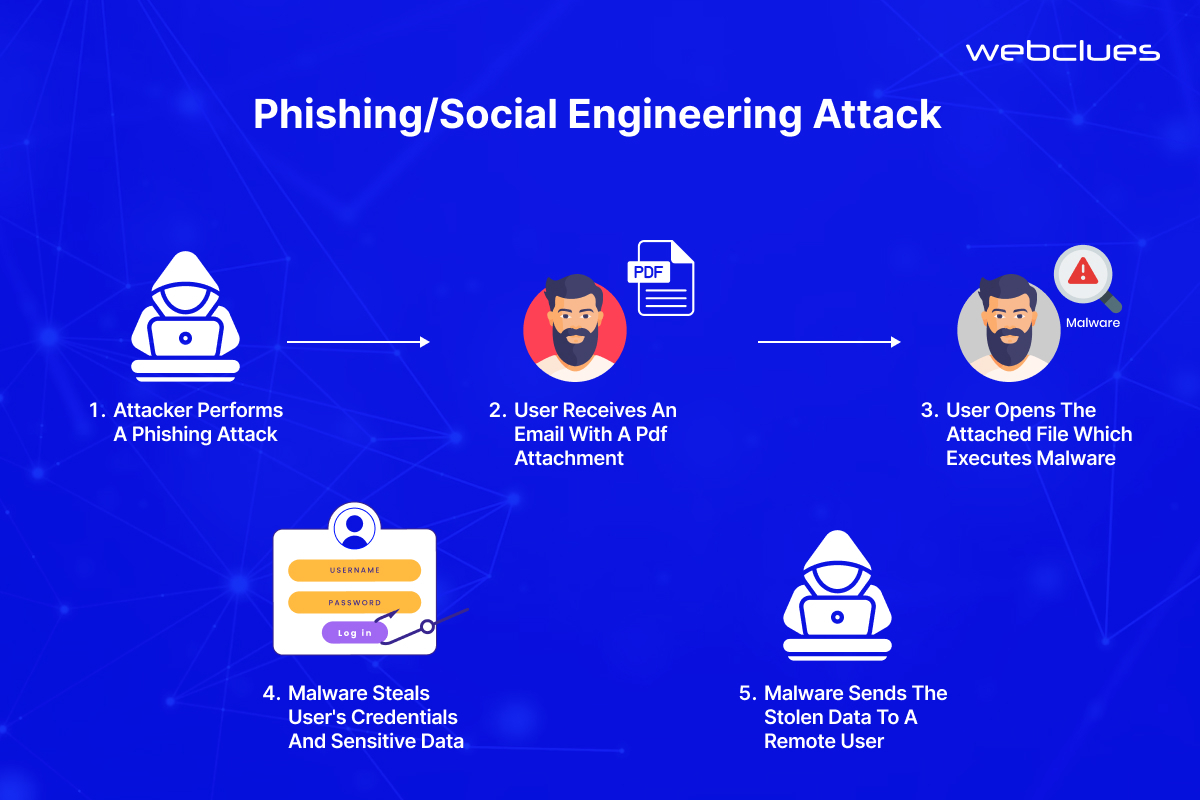
Phishing attacks are a common tactic cybercriminals use to steal sensitive information like usernames, passwords, and credit card details. They typically involve deceptive emails or fake websites designed to look legitimate. These emails may appear to be from a well-known company, bank, or even a colleague, urging the recipient to click on a malicious link or download an infected attachment. Once clicked, the link might take the victim to a fake login page that captures their credentials when entered. Alternatively, the attachment could be malware that infects the user’s device, allowing the attacker to steal data or disrupt operations.
Social engineering, on the other hand, is a broader strategy that exploits human psychology and trust. Attackers use various techniques, such as manipulation, urgency, or fear, to trick victims into revealing confidential information or taking actions that compromise security. For instance, a social engineering scam might involve a phone call impersonating IT support, requesting remote access to a user's computer under the guise of fixing a technical issue.
Here are some examples of phishing scams targeting businesses.
- Fake Invoice Scam: An email arrives claiming to be from a known vendor, with an attached invoice containing a malicious link for "payment processing."
- Urgent Account Verification: A seemingly urgent email from a popular cloud storage service prompts users to click a link to "verify their account" details.
Avoiding Phishing & Social Engineering Attacks
Phishing scams and social engineering attacks are widespread and so are their adverse effects. However, there are several steps businesses can take to substantially reduce the risk of falling victim to these attacks.
- Regularly educate employees on how to identify phishing attempts. Training should cover red flags like generic greetings, suspicious sender addresses, grammatical errors, and unsolicited attachments.
- Implementing Multi-Factor Authentication (MFA) adds an extra layer of security by requiring a second verification factor (e.g., code from a mobile app) beyond just a username and password. This makes it harder for attackers to gain access even if they steal login credentials.
- Security Email Gateways can help filter out suspicious emails before they reach employee inboxes. SEGs typically analyze email content, sender addresses, and known phishing tactics to identify and block malicious messages.
- Encourage a culture of cybersecurity awareness within your organization. This includes encouraging employees to report any suspicious activity they encounter and prioritizing cybersecurity best practices throughout the company.
Malware & Ransomware Attacks
Beyond phishing and social engineering, another major threat comes in the form of malware. This term covers a range of malicious software programs designed to infiltrate and harm computer systems. Here are some of the most common types of malware.
- Viruses: These self-replicating programs can spread quickly through networks, infecting other devices and potentially causing data corruption or system crashes.
- Worms: Similar to viruses, worms exploit vulnerabilities to spread but don't necessarily require user interaction. They can quickly overwhelm systems with network traffic.
- Trojan horses: Disguised as legitimate software, Trojans trick users into installing them. Once installed, they can steal data, create backdoors for remote access, or download other malware.
The impact of malware on businesses can be severe. Data loss, system outages, and productivity disruptions are just some of the potential consequences. However, one particularly damaging form of malware is ransomware.
Ransomware is a specific type of malware that encrypts a victim's data, essentially locking them out of their own files. Attackers then demand a ransom payment, often in cryptocurrency, in exchange for a decryption key. This can cause significant disruption to business operations, data loss, and financial strain, even if the ransom is paid.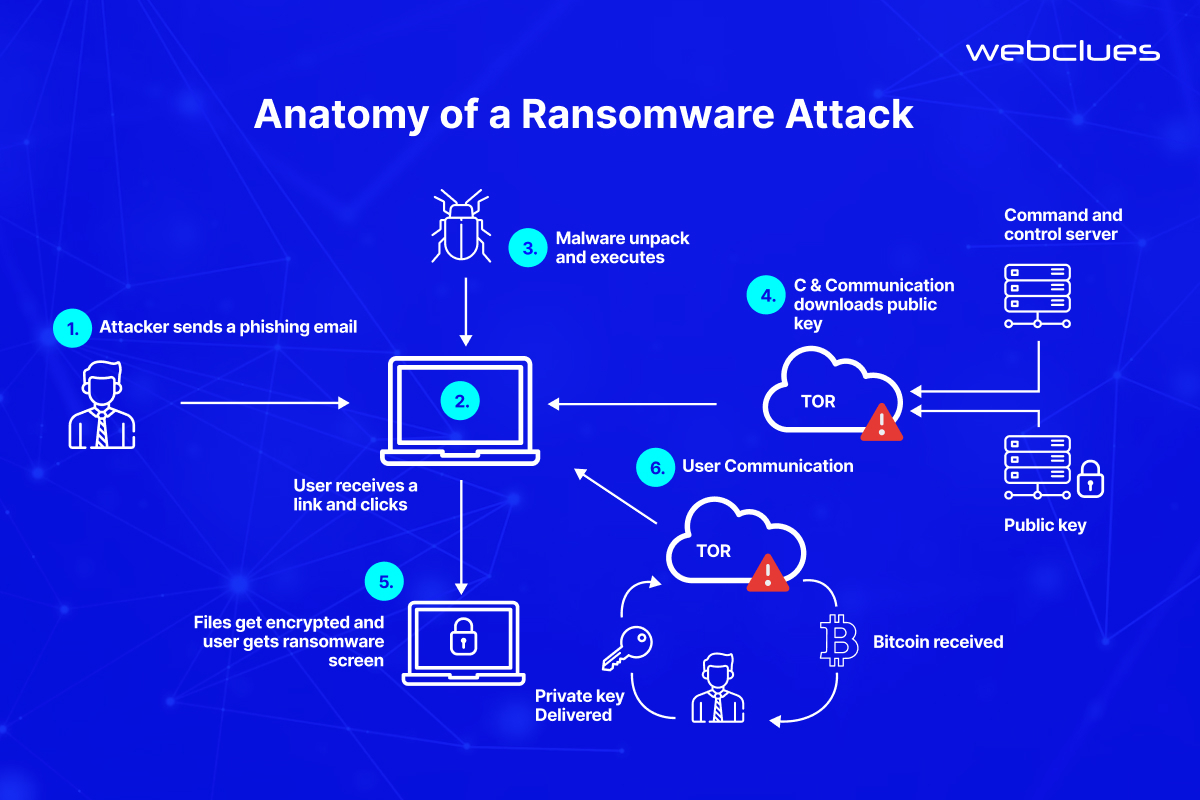
Technical Measures for Prevention
- Endpoint Detection & Response (EDR) are advanced security systems that monitor devices on a network for suspicious activity, including signs of malware infection. EDR can help detect and respond to threats in real time.
- Up-to-date anti-malware software remains a crucial line of defense. Regularly scheduled scans can identify and remove malware before it can cause damage.
- Keeping software applications and operating systems patched promptly is essential. Unpatched vulnerabilities are prime targets for malware exploitation.
- Regular data backups stored securely offline provide a critical safety net in case of a ransomware attack. Having an efficient backup and recovery plan allows businesses to restore their data without succumbing to ransom demands.
Weak Passwords & Poor Access Management
Cybersecurity threats are becoming increasingly sophisticated. Therefore, it is surprising how common a security gap weak passwords & poor access management practices are. Hackers know this, and they often target these vulnerabilities as an easy entry point. Here's how weak passwords and poor access controls can put your business at risk.
Brute-Force Attacks: Hackers can use automated tools to systematically guess passwords until they gain access. Weak passwords with limited complexity are particularly susceptible to such attacks.
Credential Stuffing: Stolen credentials from other data breaches are often used to try logging into accounts across different platforms. If users reuse passwords across work and personal accounts, a successful breach on one platform can grant access to your business systems.
Unauthorized Access: Poor access controls, such as granting excessive privileges or failing to revoke access for inactive users, create opportunities for unauthorized access, even with moderately strong passwords.
The consequences of these breaches can be severe. Hackers can steal sensitive data, disrupt operations, launch further attacks within your network, or even damage your reputation.
Mitigating the Risks
- Implement strong password policies. Enforce minimum password length requirements (ideally 12 characters or more) and complexity rules (uppercase, lowercase, numbers, symbols). Disallow dictionary words, personal information, and discourage password reuse.
- Consider implementing password managers. These secure applications store and manage complex passwords for different accounts, eliminating the need for users to remember or reuse weak passwords.
- Multi-Factor Authentication (MFA) adds a crucial second layer of security beyond passwords. When logging in, users are prompted for a second verification factor significantly reducing the risk of unauthorized access even if a password is compromised.
- Regularly review and disable dormant user accounts that haven't been active for a set period. This minimizes potential attack surfaces by eliminating unused accounts that could be exploited if compromised credentials are found elsewhere.
- Access control mechanisms dictate which users can access specific systems and data. The "least privilege principle" emphasizes granting users only the minimum level of access necessary to perform their job functions. This reduces the potential damage if an attacker gains unauthorized access using a compromised credential.
- Penetration testing can simulate real-world attacks to identify weaknesses in password complexity, access controls, and overall security posture. This helps uncover areas for improvement before attackers exploit them.
Evolving Cloud Threats & Supply Chain Risks
The rapid adoption of cloud computing has revolutionized how businesses operate but it has also introduced new security challenges. As more data and applications migrate to the cloud, the attack surface for cybercriminals expands quite notably. The following threats warrant special attention from cloud environments.
Growing Attack Surface: Cloud infrastructure is inherently complex and distributed. Misconfigurations in cloud settings, vulnerabilities in cloud services, or insecure APIs can create openings for attackers to exploit.
Supply Chain Attacks: Businesses increasingly rely on a network of third-party vendors and cloud service providers. A vulnerability in a single vendor within the supply chain can be used as leverage to attack your core systems. This is known as a supply chain attack.
Eliminating Cloud Risks and Supply Chain Weaknesses
- Choose reputable cloud service providers with a proven track record of security and a strong commitment to data protection. Evaluate their security practices, compliance certifications, and incident response protocols.
- Implement effective security measures within your cloud environment. This includes encryption of data at rest and in transit, access controls to restrict unauthorized access and continuous monitoring for suspicious activity.
- Exercise vendor risk management. Don’t overlook the security posture of your vendors. Conduct thorough vendor risk assessments to understand their security practices and potential vulnerabilities. Include security clauses in contracts to ensure vendors maintain adequate security controls.
Insider Threats & The Human Element
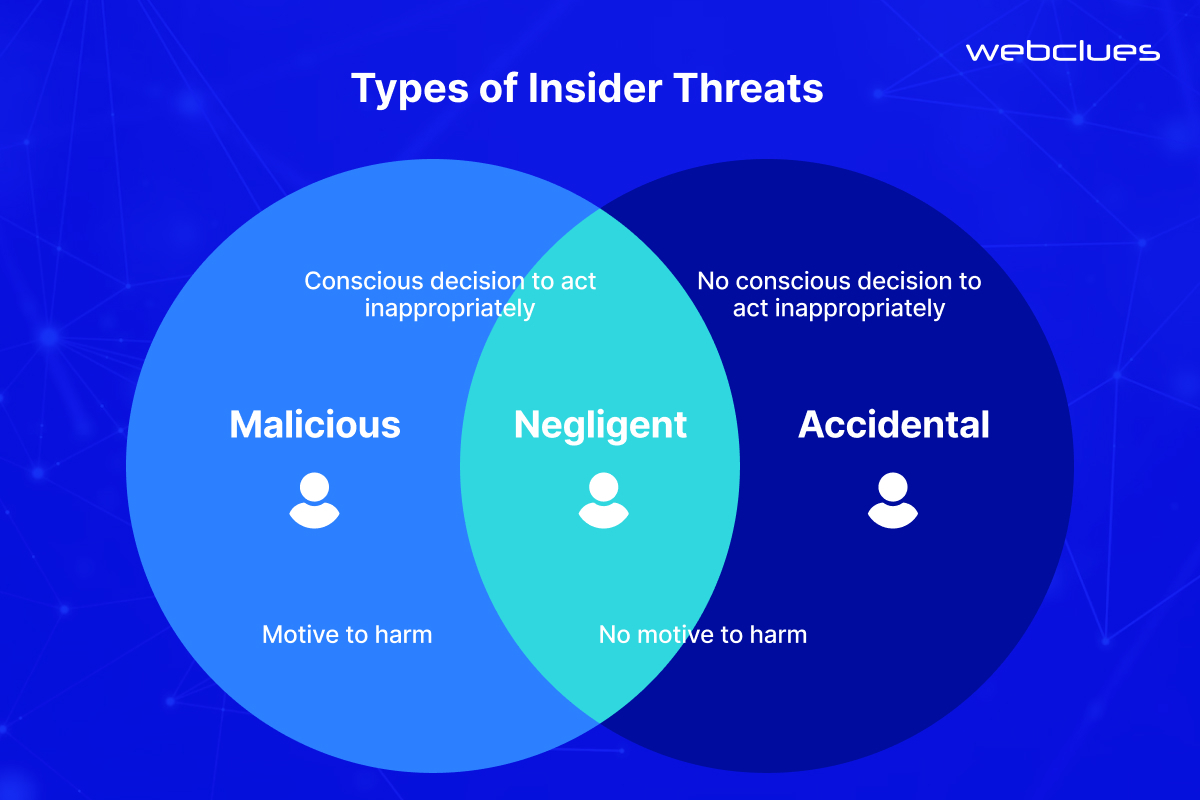
Often overlooked, insider threats pose a significant and growing cybersecurity concern. Unlike external attackers, insider threats originate from within your organization, typically from authorized users with legitimate access to your systems and data. These insiders can be employees, contractors, or even temporary workers. The motivations behind insider threats can vary.
- Malicious Intent: Disgruntled employees, disgruntled ex-employees, or individuals with criminal motives may intentionally misuse their access to steal data, disrupt operations, or sabotage systems.
- Negligence: Careless employees who fail to follow security protocols, or those who click on suspicious links or attachments, can unknowingly introduce vulnerabilities that attackers can exploit.
- Accidental Leaks: Human error can also play a role. Sharing sensitive information inadvertently through emails, social media, or even casual conversations can lead to data breaches.
Mitigating the Insider Threat
- While completely eliminating insider threats might not be possible, there are steps you can take to considerably reduce the risk.
- Implementing user activity monitoring (UAM) tools can help detect unusual access patterns or suspicious activity within your network. This can raise red flags for potential insider threats.
- Data Loss Prevention (DLP) solutions can be deployed to monitor and control data movement across your network. DLP can identify and prevent sensitive data from being exfiltrated (copied or transferred outside) by unauthorized users, intentionally or accidentally.
- Conducting thorough background checks on potential employees and contractors is crucial. Additionally, ongoing security awareness training programs can educate employees on identifying and reporting suspicious activity, proper data handling procedures, and the importance of cybersecurity best practices.
Building a Culture of Cybersecurity
Cybersecurity threats are constantly evolving and thus demand persistent vigilance. Furthermore, attackers are constantly developing new methods to exploit vulnerabilities. Businesses can't afford to be reactive.
A proactive approach and building a strong culture of cybersecurity within your organization are essential for long-term success. This involves not only implementing the technical safeguards discussed throughout this blog but also promoting a security-conscious mindset among your employees.
At Webclues Infotech, we are passionate about helping businesses tackle cyber threats. We offer a comprehensive suite of cybersecurity solutions designed to protect your data, systems, and reputation.
Contact us today for a free consultation or cybersecurity assessment to discuss your specific needs and identify potential vulnerabilities. Let's work together to build a more secure future for your organization.
Build Your Agile Team
Hire Skilled Developer From Us
Improve your security posture with comprehensive cybersecurity services from WebClues Infotech
Want to identify and address security weaknesses? Webclues' expert cybersecurity services can help you identify potential risks and fix vulnerabilities before a breach.
Book Free Consultation!Our Recent Blogs
Sharing knowledge helps us grow, stay motivated and stay on-track with frontier technological and design concepts. Developers and business innovators, customers and employees - our events are all about you.
Contact
Information
Whether you're building next door or across time zones, we stay close in ideas, in execution, and in support.
India

Ahmedabad
1007-1010, Signature-1,
S.G.Highway, Makarba,
Ahmedabad, Gujarat - 380051
Rajkot
1308 - The Spire, 150 Feet Ring Rd,
Manharpura 1, Madhapar, Rajkot, Gujarat - 360007
UAE
Dubai
Dubai Silicon Oasis, DDP,
Building A1, Dubai, UAE
USA
Atlanta
6851 Roswell Rd 2nd Floor, Atlanta, GA, USA 30328
New Jersey
513 Baldwin Ave, Jersey City,
NJ 07306, USA
California
4701 Patrick Henry Dr. Building
26 Santa Clara, California 95054
Australia
Queensland
120 Highgate Street, Coopers Plains, Brisbane, Queensland 4108
UK
London
85 Great Portland Street, First
Floor, London, W1W 7LT
Canada
Burlington
5096 South Service Rd,
ON Burlington, L7l 4X4
Let’s Transform Your Idea into Reality. Get in Touch