Use of Machine Learning to Improve IoT Security: Opportunities and Challenges
Internet of Things (IoT) is expanding at a rapid pace, with billions of devices connected to the Internet. Prevalent everywhere, be it homes, offices, healthcare facilities, manufacturing industries, etc., these devices exchange a considerable amount of data over the internet. It is estimated that the number of IoT devices, which was 8 billion in 2019, will grow to 41 billion in 2027. Such rapid growth of IoT has led to tremendous advancements in multiple industries, revolutionizing the way we work and live. However, an increase in the number of connected devices has made IoT networks more vulnerable to cyberattacks, which themselves are getting more sophisticated by the day. Moreover, IoT devices are often resource-constrained and have limited security features. As a result, traditional security methods like firewalls and intrusion detection systems are not as effective in protecting IoT networks.

Amidst this major concern surrounding IoT security, the integration of machine learning (ML) techniques with it holds great promise in addressing these challenges and safeguarding our interconnected world.
Opportunities Associated with the Use of Machine Learning
Adopting a machine learning (ML) approach to IoT security can present significant opportunities for improving the protection of interconnected devices and systems. From device-level anomaly detection to automated threat response – ML offers distinct capabilities that can help IoT security teams make intelligent predictions and responses.
Let’s explore several principal opportunities associated with the usage of machine learning to enhance IoT security.
Anomaly and Intrusion Detection:
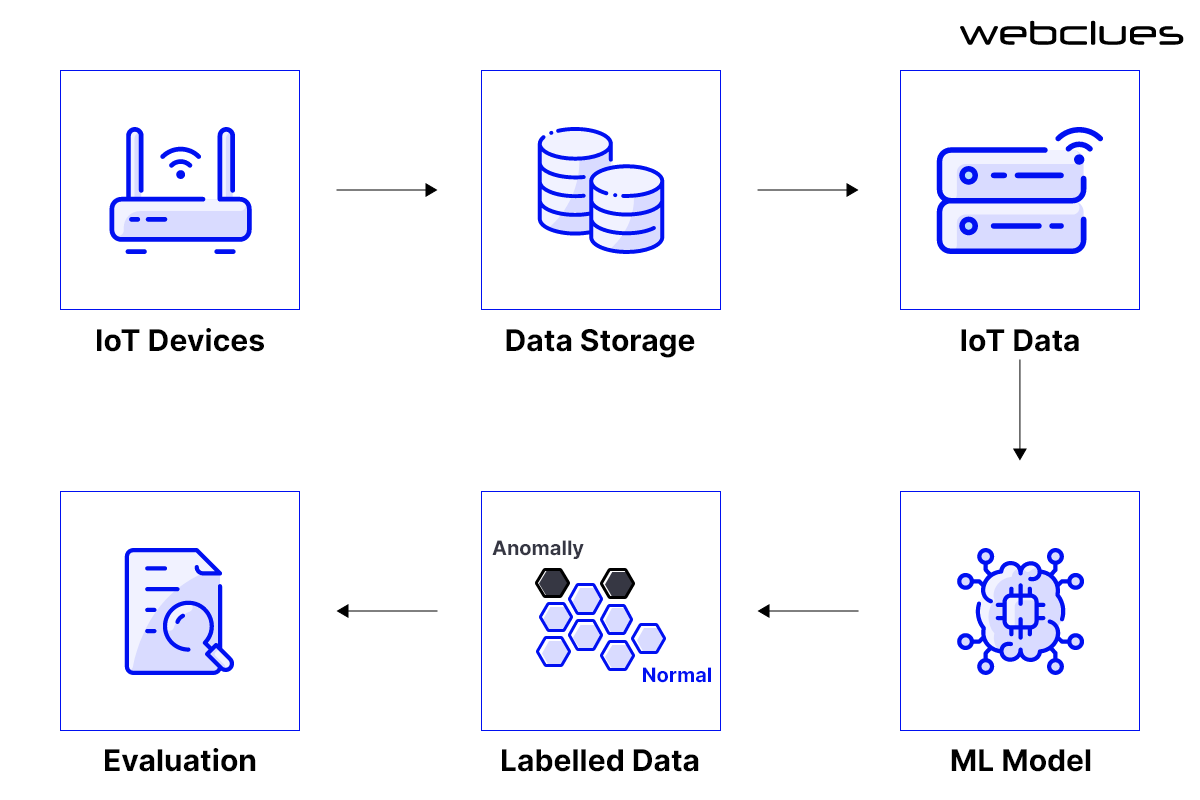
IoT generates a vast amount of data, which provides valuable information about device behavior. Machine learning algorithms can be trained to analyze and monitor this data for patterns that indicate anomalies and potential security threats. ML models can detect abnormal activities like unusual login attempts or suspicious traffic patterns and can trigger alerts. This enables timely response to potential threats and mitigation of risks before they cause damage. For instance, if a connected device starts generating an unusual amount of traffic or sending data to unknown destinations, the ML model can mark it as a potential security breach.
Predictive Maintenance:
The wealth of data that IoT devices generate can be utilized to predict vulnerabilities and device failures. Machine learning algorithms can identify potential security risks by analyzing historical data patterns. These proactive predictions of risks before they are exploited enable organizations to ensure the continuous and safe operation of their IoT infrastructure. To exemplify this, ML models can recommend required updates or patches by identifying patterns that indicate device degradation or vulnerabilities and thus help mitigate security risks.
Behavioral Profiling:
Machine learning algorithms can be utilized to generate behavior profiles of IoT devices. ML models can monitor device interactions and collect data on usage patterns, based on which, they can establish baseline behaviors. If a deviation from these baselines is found, it may indicate security breaches or unauthorized access attempts. This becomes especially useful when certain devices connect intermittently or send or receive data using legacy protocols. The behavior of these devices is easier to track if they become active or become the target of an attack. ML models can efficiently detect such a potential “hidden” device as they can recognize an increase in network traffic at a particular location by automatically scanning and comparing historical network behavior. This can help IT managers incorporate such devices in their security plans in the future.
Secure Authentication:
Passwords and other traditional authentication mechanisms are often insufficient to ensure the security of IoT devices. It is possible to enhance authentication methods by incorporating machine learning into IoT security. It can do so by analyzing various factors, such as device location, user behavior, and biometric data. ML can analyze device location patterns and user behavior and determine if a login attempt is originating from an unfamiliar location or if the behavior of a user accessing a device is inconsistent with their typical usage. This can help deploy additional security measures and mitigate the risk of damage.
Challenges Posed by the Use of Machine Learning
Evidently, using machine learning to improve IoT security offers numerous advantages. However, before hiring IoT developers, it is important to consider several challenges such as data privacy, resource constraints, adversarial attacks, and model interpretability. Let’s explore them in detail.

Data Privacy and Protection
Machine learning collects and analyzes massive amounts of sensitive data to enhance IoT security. It is a significant challenge to ensure the privacy and protection of this data. This requires organizations and companies to implement robust encryption, access control mechanisms, and anonymization techniques to protect user information. Moreover, it becomes mandatory to define clear policies and regulations governing data privacy in the context of IoT security through machine learning.
Resource Constraints
Machine learning algorithms are usually resource-intensive. This makes it challenging to deploy these algorithms directly on IoT devices as they often have limited computational power and memory. So implementing ML-based security solutions requires balancing the need for robust securities with the constraints of IoT devices, which is a crucial task to execute. There is one plausible solution to this, which includes deploying the more powerful ML models on edge devices or cloud servers and offloading the computational tasks there.
Adversarial Attacks
Adversarial attacks involve malicious actors manipulating input data to deceive the system. ML models are vulnerable to these attacks as they can bypass security measures, compromising the integrity and reliability of IoT systems. It is still an ongoing challenge to develop robust ML models that can resist such attacks. However, it is possible to enhance the resilience of these models against these attacks by using techniques such as adversarial training and input validation.
Model Interpretability
Transparency and comprehensibility are crucial aspects that machine learning models should possess to gain the trust of users as well as security professionals. A considerable hurdle in adopting ML-based security solutions is interpreting complex ML models and providing meaningful explanations for their decisions. It is imperative to address this challenge in order to increase transparency and facilitate trust. For this, efforts are being made to develop interpretable machine learning models, along with the techniques to explain the decision-making process of black-box models.
The Final Verdict
The use of machine learning in IoT security can certainly safeguard our interconnected world and unlock the full potential of IoT technology. The opportunities discussed above are proof of it. However, the subsequent challenges need to be carefully addressed to build a more secure and resilient IoT ecosystem and leverage these benefits.
If you need to learn more about ML-based solutions for IoT security, at WebClues, we can help. We offer comprehensive IoT consulting and development services based on your unique requirements. Get in touch with us today and one of our friendly team members will be more than happy to help!
Build Your Agile Team
Hire Skilled Developer From Us
Want to know how the security of your IoT devices can be optimized?
Backed by years of experience, our IoT experts can help you with their professional guidance, whatever the issue.
Get a Free ConsultationOur Recent Blogs
Sharing knowledge helps us grow, stay motivated and stay on-track with frontier technological and design concepts. Developers and business innovators, customers and employees - our events are all about you.
Contact Information
Let’s Transform Your Idea into Reality - Get in Touch
India
Ahmedabad
1007-1010, Signature-1,
S.G.Highway, Makarba,
Ahmedabad, Gujarat - 380051
Rajkot
1308 - The Spire, 150 Feet Ring Rd,
Manharpura 1, Madhapar, Rajkot, Gujarat - 360007
UAE
Dubai
Dubai Silicon Oasis, DDP,
Building A1, Dubai, UAE
USA
Delaware
8 The Green, Dover DE, 19901, USA
New Jersey
513 Baldwin Ave, Jersey City,
NJ 07306, USA
California
4701 Patrick Henry Dr. Building
26 Santa Clara, California 95054
Australia
Queensland
120 Highgate Street, Coopers Plains, Brisbane, Queensland 4108
UK
London
85 Great Portland Street, First
Floor, London, W1W 7LT
Canada
Burlington
5096 South Service Rd,
ON Burlington, L7l 4X4